Bandiz Technoz + Google Cloud
Bandiz for GCP
Autonomous Data Protection
For all cloud native and non-native data systems and applications on GCP
Sensitive
Data Intelligence
Understanding sensitive data in both dark and native data systems on GCP.
Security
Establish a distributed mesh for data visibility and security across GCP.
Privacy
With Robotic automation, PrivacyOps simplifies privacy management.
Governance
& Compliance
Attain comprehensive compliance with worldwide data regulations.
Sensitive Data Intelligence
- Shadow Data
Asset Discovery - Data Discovery
Classification & Labelling - Sensitive
Data Catalog - People
Data Graph - Security Posture
& Misconfigurations - Data
Risk Graph
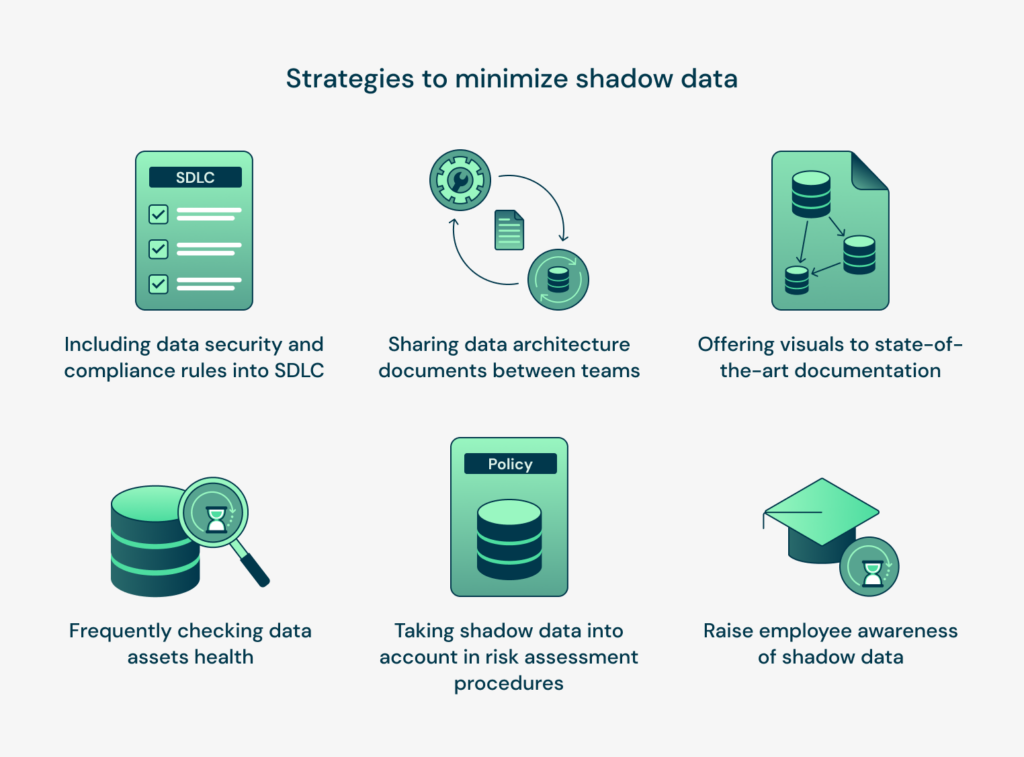
Shadow Data
Asset Discovery
Asset Discovery
Automatically discover all your dark and native data assets across GCP footprint across accounts, regions and geographics
Data Discovery
Classification & Labelling
Classification & Labelling
Automatically detect, categorize, and tag numerous sensitive data items within structured and unstructured GCP data systems at a petabyte scale.

Sensitive
Data Catalog
Data Catalog
Construct catalogs for sensitive data in structured and unstructured formats & effortlessly locate particular sensitive data within your GCP presence.

People
Data Graph
Data Graph
Automate the creation of a graph linking individuals to their personal data. This forms the basis for fulfilling data subject rights obligations automatically.

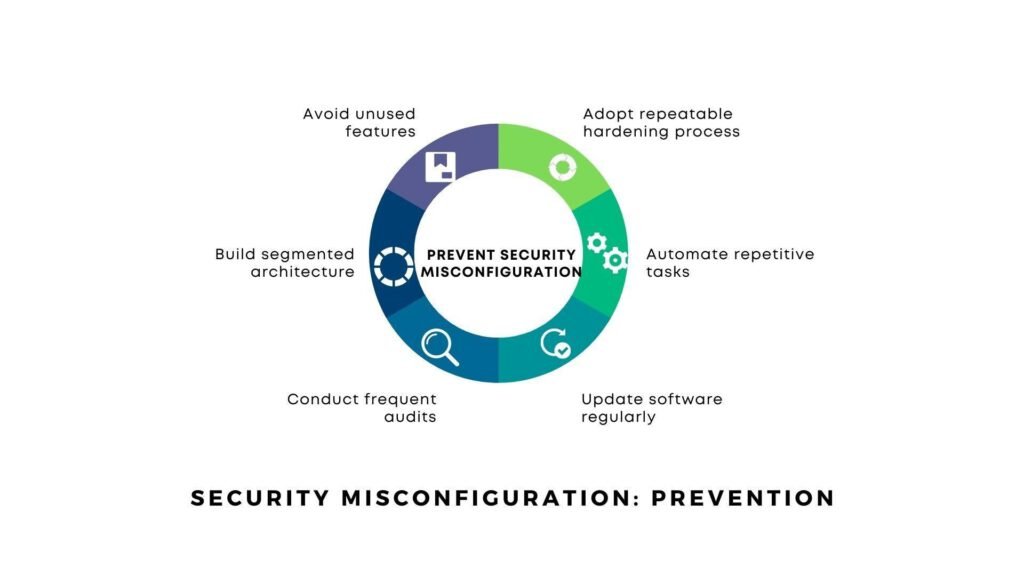
Security Posture
& Misconfigurations
& Misconfigurations
Identify security misconfigurations and risks in GCP data systems and automatically rectify misconfigurations.
Data
Risk Graph
Risk Graph
Detect and rank external and internal data risks using a risk scoring and attribution system.

Security
Identify high-risk data and enable necessary protections accordingly.
Privacy
Single automated platform for global data privacy compliance, PrivacyOps solution.
Governance & Compliance
Satisfy data governance demands effectively and efficiently.
Security
- Monitor Data Risk
- Enforce Data Protection
- Govern Sensitive Data Access
- Investigate Security Issues
Monitor Data Risk
Uncover hidden data risks
Reveal concealed data risks by identifying hotspots within your Workday instance through uncovering data risks.
Enforce Data Protection
Enable Protections
Empower safeguards by identifying security misconfigurations linked to your Workday instance and implementing automatic remediation.
Govern Sensitive Data Access
Control Access
Consistently audit users and groups with access to sensitive data in Workday, refining policies as needed.
Investigate Security Issues
Investigate Security Issues
Conduct ongoing audits of users and groups with access to sensitive data in Workday, while refining policies as necessary.
Privacy
- Data Mapping Automation
- DSR Robotic Automation
- Assessment Automation
- Consent Automation
- Data Incident Mng
Data Mapping Automation
Always up to date data maps and records of processing
Maintain current data maps and processing records. Automate privacy measures, DPIAs, and Article 30 reports using sensitive data insights.DSR Robotic Automation
Automate fulfillment of individual rights
Automate the process of fulfilling individual rights. Automatically meet data subject requests and retain evidence of compliance.
Assessment Automation
Automate DPIAs and Privacy-by-Design
Automate DPIAs and Privacy-by-Design. Centralize collaboration and tracking for all assessments in a unified platform for efficiency.
Consent Automation
Capture and honor user consent automatically
Automatically capture and respect user consent. Utilize data in accordance with cookie consent and universal consent principles.
Data Incident Mng
Guidance for Data Incident Response and Reporting
Automate Data Incident Response and Reporting Streamline incident response by collecting details, defining scope, and tailoring notifications to meet global privacy regulations.
Compliance
Continuously track alterations and deviations in data, security configurations, and access protocols for automated remediation. Align up-to-date security controls with diverse compliance standards like ISO, NIST, PCI, HIPAA, GLBA, GDPR, ensuring perpetual compliance. This proactive approach guarantees that security measures remain current, reflecting a commitment to robust data protection and adherence to industry-specific regulations.
Data Security Regulations
Data Privacy Regulations

Covering Everywhere You Have Data
With 1000+ integrations across data systems



























