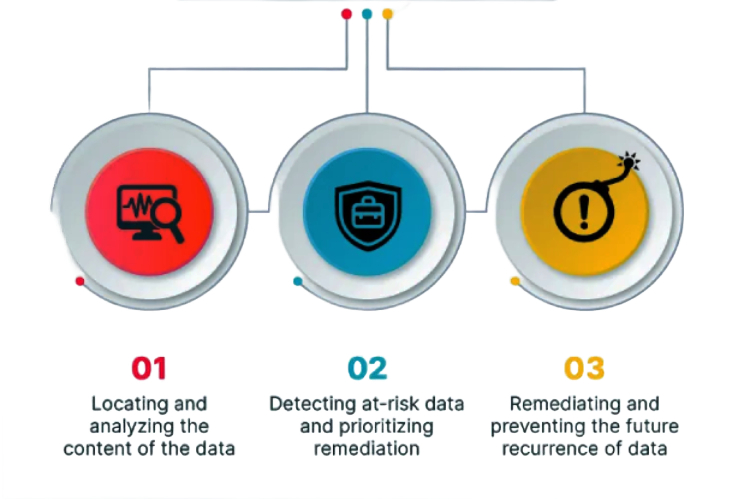
Data Security Posture Management (DSPM)
Components Of DSPM
Continuous Monitoring
Risk Assessment
Compliance Management
Policy Enforcement
Incident Response
User Access Control
Discover & Catalog All Data Assets
Attain a holistic perspective of data assets spanning public clouds, data clouds, SaaS, and on-premises environments. Uncover both shadow and managed data assets for enhanced visibility. Automate the registration of datasets into structured and unstructured data catalogs, promoting efficient management and governance. This streamlined approach ensures a unified view of the organization’s data landscape while minimizing the risk associated with undiscovered data sources

Gain Contextual Data Intelligence
Harness the power of artificial intelligence for precise classification of sensitive data across diverse systems, encompassing structured, semi-structured, and unstructured formats, all at a scalable magnitude. Obtain contextual data insights, encompassing ownership details, regulatory compliance obligations, and pertinent security and privacy metadata. This AI-driven approach not only ensures accuracy in data classification but also provides valuable contextual information, enabling organizations to navigate compliance requirements effectively and bolster overall data security measures.
Prevent Unauthorized Data Access

Ensure Consistent Data Controls Across Flows
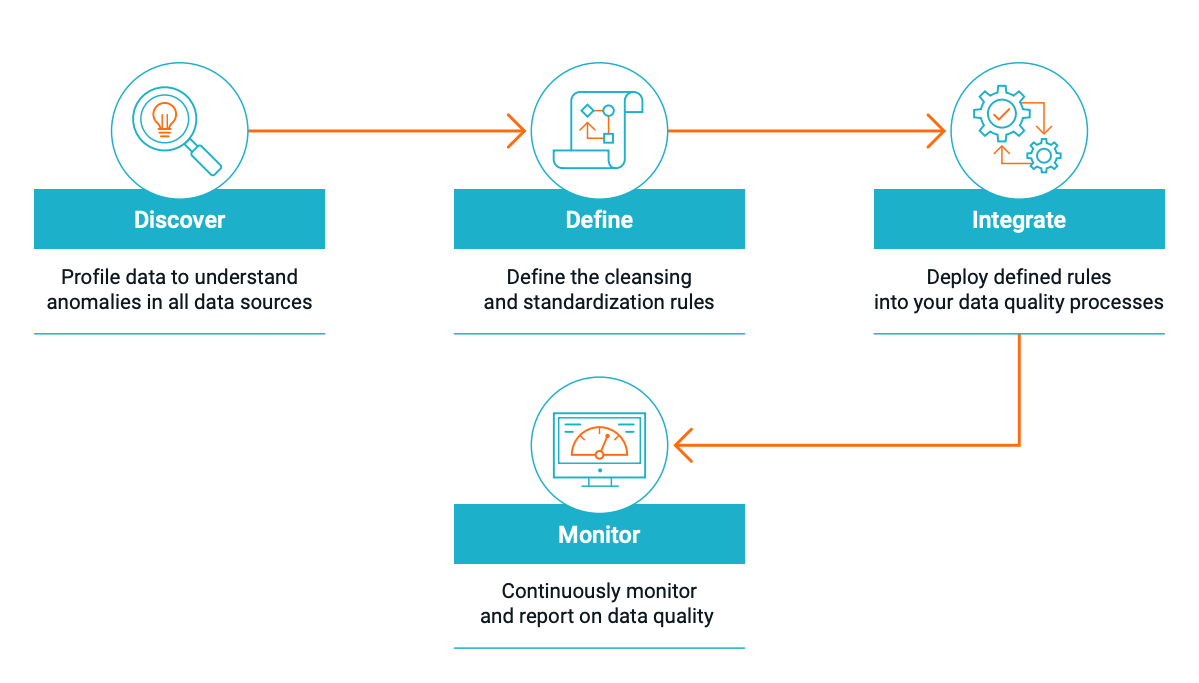
DSPM Learning Resources

Online Courses
Webinars and Virtual Events

Blogs and Articles
Covering Everywhere You Have Data
With 1000+ integrations across data systems